)
The dual face of artificial intelligence in data protection and privacy
In the digital age, artificial intelligence stands as a double-edged sword, presenting both significant risks and promising solutions for data protection and privacy. We help our customers to clarify the complex interactions of AI within the cybersecurity realm, especially for organizations and people not fully aware of AI techniques and considering the rapid evolutions of the sector.
AN INTRODUCTION
What does AI mean for security?
In order to explore the significant impact AI has on data protection and privacy, the first section of this article was entirely crafted using AI tools. What follows is an exact transcription of the AI-generated content, based on a straightforward prompt: "Let us analyze with AI what AI means for security." The second part of the article will examine the findings in depth, placing a strong emphasis on how AI technologies reshape the landscape of data security, privacy protection, and regulatory compliance in an increasingly digital world.
The text generated by AI
AI: a boon and bane
Artificial Intelligence, by its very design, seeks to mimic human intelligence through complex algorithms and data processing. This capability allows AI to analyze vast amounts of data, identify patterns, and make decisions with unprecedented speed and accuracy. However, this very strength of AI also introduces new avenues for cyber threats.
The risks posed by AI
AI's potential to transform industries is undeniable, but it also introduces novel risks to data protection and privacy. Here are some key concerns:
Data breaches: AI systems require large datasets to function effectively. These datasets often contain sensitive personal information, making them prime targets for cybercriminals. A breach in such systems can lead to the exposure of massive amounts of personal data.
Automated attacks: Hackers leverage AI to automate and scale their attacks. AI-driven malware can adapt to security measures, making it more difficult to detect and counter. For instance, AI can generate phishing emails that are highly personalized, increasing the likelihood of unsuspecting individuals falling victim to such scams.
Deepfakes: AI technology can create realistic but fake images, audio, and videos. These deepfakes can be used for malicious purposes, such as blackmail or spreading misinformation, further complicating the landscape of data protection.
AI in the hands of hackers
As AI technology evolves, so do the tactics of cybercriminals. Hackers are increasingly using AI to develop sophisticated attack methods that challenge traditional security measures. Here are some examples:
AI-powered phishing: Traditional phishing attacks often rely on generic messages sent to large groups of individuals. AI, however, can analyze social media profiles, emails, and other online activities to craft highly customized phishing emails that are difficult to distinguish from legitimate communications.
Adaptive Malware: AI enables malware to learn from its environment and adapt its behavior. This means that once inside a system, AI-powered malware can modify its tactics to avoid detection by traditional antivirus software.
Advanced Persistent Threats (APTs): Hackers can use AI to carry out long-term, targeted attacks known as APTs. AI helps these attacks remain undetected while infiltrating networks and gathering sensitive data over extended periods.
The protective power of AI
Despite these risks, AI also offers powerful tools to enhance cybersecurity and protect data. When used responsibly, AI can be a formidable ally in the fight against cyber threats. Here are some ways AI can help:
AI for threat detection and prevention
AI can analyze vast amounts of data in real-time, identifying anomalies and potential threats much faster than human analysts. Some key applications include:
Behavioral analysis: AI can monitor user behavior patterns and detect deviations that may indicate a security breach. For instance, if an employee's login activity suddenly shifts to unusual hours or locations, AI can flag this behavior for further investigation.
Intrusion Detection Systems (IDS): AI-powered IDS can identify and respond to network intrusions in real-time, minimizing the damage caused by cyber-attacks.
Automated response: AI can automate the response to certain types of cyber threats. For example, if a phishing email is detected, AI can automatically quarantine the email and alert the user, reducing the risk of it being opened.
AI in data protection
AI can also play a crucial role in safeguarding personal data:
Data encryption: AI can enhance data encryption techniques, making it harder for unauthorized parties to access sensitive information.
Access control: AI can manage access to data by continuously assessing the risk level of users and adjusting permissions accordingly. This ensures that only authorized individuals have access to sensitive information.
Data masking: AI can mask sensitive data in non-production environments, allowing organizations to use real data for testing and development without compromising privacy.
How Reply can help
At Reply, we understand the complexities of navigating the dual nature of AI in cybersecurity. Our team of experts is dedicated to leveraging AI to provide robust data protection solutions while mitigating the associated risks. Here is how we can assist:
Comprehensive risk assessment: We conduct thorough risk assessments to identify potential vulnerabilities in your AI systems and recommend measures to address them.
AI-driven security solutions: We develop and implement AI-driven security solutions tailored to your specific needs, enhancing your ability to detect, prevent, and respond to cyber threats.
Ongoing monitoring and support: Our services include continuous monitoring and support to ensure your systems remain secure against evolving threats.
Training and awareness programs: We offer training programs to educate your staff on the latest AI-driven threats and how to mitigate them. Awareness is a crucial component of a robust cybersecurity strategy, and our training ensures that your team is well-prepared to handle potential threats.
Customized AI solutions: Recognizing that each organization has unique needs, we develop customized AI solutions to address your specific security challenges. Whether it is enhancing data encryption, implementing advanced threat detection systems, or developing automated response protocols, our tailored solutions ensure comprehensive protection.
Conclusions
In conclusion, while AI presents significant challenges to data protection and privacy, it also offers powerful tools to counteract these threats. By working with experts like those at Reply, organizations can harness the protective power of AI while safeguarding against its risks. Together, we can navigate this complex landscape and ensure a secure digital future.
The dual nature of Artificial Intelligence in cybersecurity demands a balanced approach. As we continue to innovate and develop AI technologies, we must remain vigilant about the potential risks while embracing the opportunities they present. By fostering collaboration between AI developers, cybersecurity experts, and organizations, we can create a safer digital environment for all.
At Reply, we are committed to leading the charge in this endeavor, providing cutting-edge AI-driven security solutions that empower organizations to protect their data and privacy effectively. As we move forward, our focus remains on innovation, adaptability, and excellence in cybersecurity, ensuring that we stay ahead of the evolving threats and continue to deliver unparalleled protection to our clients.
The conclusions
An overview of what AI generated for us
As you may see, the AI worked perfectly, it created a perfect article showing exactly what is useful to understand the cyber risks and the potentialities of AI and we had a very good example of its power.
Nevertheless, there is something a bit concerning about it too. It is not fully clear where this information came from, either from the training data of AI model or from personal data where it has access to. And in case the AI tool in use is connected with external Web (this was not our case, but it is a common use case), it could have been “poisoned” with wrong or dangerous information, it could have been infected with malware, it could have used and therefore exposed personal and sensitive data of the user where it has access. In general, it means that to use AI in every aspect of our life, and especially when it means touching the physical world, we must put in place a set of controls that could certify the results of AI, check that all the security levels are respected and that the result is in line with policies, regulations and ethical values of our companies and of our society.
This core belief is at the heart of Reply's approach to AI, ensuring that all initiatives across the organization adhere to ethical guidelines, with a focus on Responsible AI development and collaboration with external stakeholders.
Security for AI
Based on these ethical principles, Reply security experts developed a complete AI Security Governance and Compliance framework to manage AI systems setup and operations, with strong Cyber Security controls and tools to protect data and users.
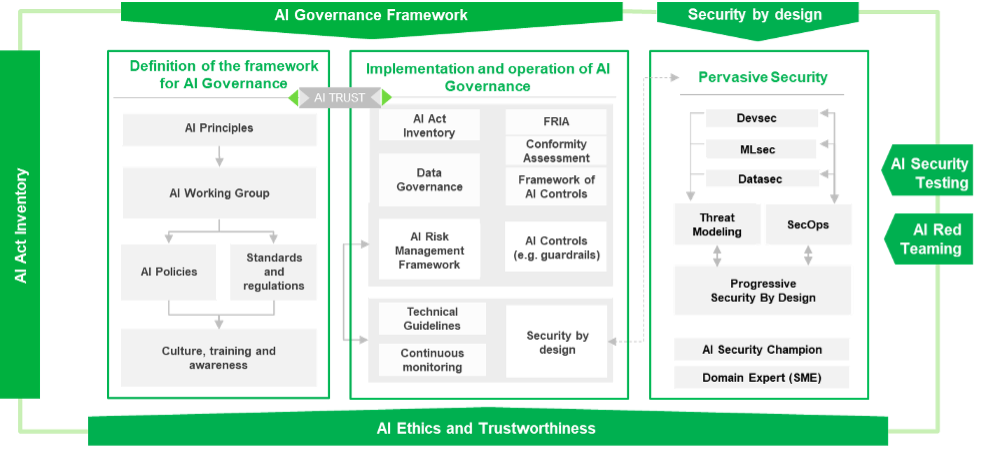
The setup of the AI Framework is a fundamental step to be planned as a short-term action, considering two main factors.
The first factor is that the AI use cases that are currently present in the market are exiting from the innovation sphere and will become very soon real production applications. They are in fact using real data also on these initial use cases, being already a big concern for the CISO and CSO organizations, and they will represent an increasing risk once they will be widely used by end customers and spread on the complex digital environment present in every company.
Analyzing and securing the cyber risks related to AI tools and techniques, will therefore be a key element to protect the investments, with Cyber Security organizations playing a key role on AI adoption.
The second factor is related to the AI Act Compliance, which requires the adoption of dedicated organization and processes to analyze and classify every AI usage in the company. The main responsibilities will be in charge of the companies using high risk AI systems, but this means that every company must track all AI usage, realizing the AI Inventory, define principles and policies and classify the AI systems in use.
The project’s approach proposed by Reply is tailor made, namely aimed to design and implement a framework specific and focused on the company’s context, and specifically integrated into the taxonomies and methodologies already defined and applied from Compliance and Cyber Security organizations.
AI for Security
In addition to the activities necessary to protect AI tools and data, Cyber Security could absolutely benefit from the power of AI. To fully exploit this opportunity, it is fundamental to know very well how to use AI powerful tools to achieve results, while reducing risks and applying all relevant controls.
For this reason, Reply is using AI to develop Security agents, trained on two areas where major needs are present for security-related tasks and processes: the Secure SDLC, with AI agents supporting development team to introduce security requirements and testing in a shift-left approach, and the DORA regulation supporting agents.
The DORA regulation is a good example of how AI can be used to support Security and Compliance organizations, with a careful selection of specialized and properly trained agents that can help streamline document and contract analysis processes that are required for compliance and that need several trained people to be accomplished.
Reply always adopts a careful balance between innovation, real process needs, and regulatory constraints when selecting which functionalities to implement with these agents. Our goal is to ensure that the solutions we develop not only push the boundaries of technological capabilities but also meet practical business requirements and comply with existing standards and regulations. This approach allows us to create AI-driven tools that are both cutting-edge and pragmatic, delivering real value while maintaining a high level of trust and security.

Spike Reply specializes in security advisory, system integration and security operations and supports its clients from the development of risk management programs aligned with corporate strategic objectives, to the planning, design and implementation of all the corresponding technological and organizational measures. With a wide network of partnerships, it selects the most appropriate security solutions and allows organizations to improve their security posture.
;Resize,width=660)
,allowExpansion;Resize,width=660)
,allowExpansion;Resize,width=660)
;Resize,width=660)
,allowExpansion;Resize,width=660)