)
NIS 2
The Pillar Of European Cybersecurity
Scenario
The threat landscape in the Network domain in Italy is extremely diverse and constantly evolving, with our country reaffirming itself as one of the prime targets for cybercriminals. The information contained in the latest CLUSIT 2024 report provides a detailed and up-to-date overview of the different types of attacks that shape the Network Security scene. Attacks in this field span a wide range of vectors, from system vulnerabilities—whether already known or newly discovered—to social engineering attacks, where criminals attempt to deceive users through fraudulent communications.
Main impacts
The report's data highlight how cybercriminals favor two particularly harmful types of attacks: malware—malicious software designed to damage or compromise network systems—and DDoS (Distributed Denial of Service) attacks, which aim to make online services inaccessible by overwhelming a system's resources. Statistics show that malware and DDoS attacks account for 32.6% and 30.3% of reported incidents, respectively. In this context, the focus is on these types of attacks to develop innovative and effective solutions to mitigate damage and enhance system resilience.
The economic damage caused by these threats is significant. In 2024, the average cost of a data breach in Italy reached €4.37 million, a figure that reflects not only the direct damage from data loss or compromise but also the recovery costs and potential legal actions.
Regarding phishing, the average cost per breach amounts to €4.18 million, while credential theft or compromise raises the figure to €4.75 million. Social engineering—one of the most insidious techniques used to manipulate individuals and gain access to confidential information—has an average cost of €4.78 million per incident.
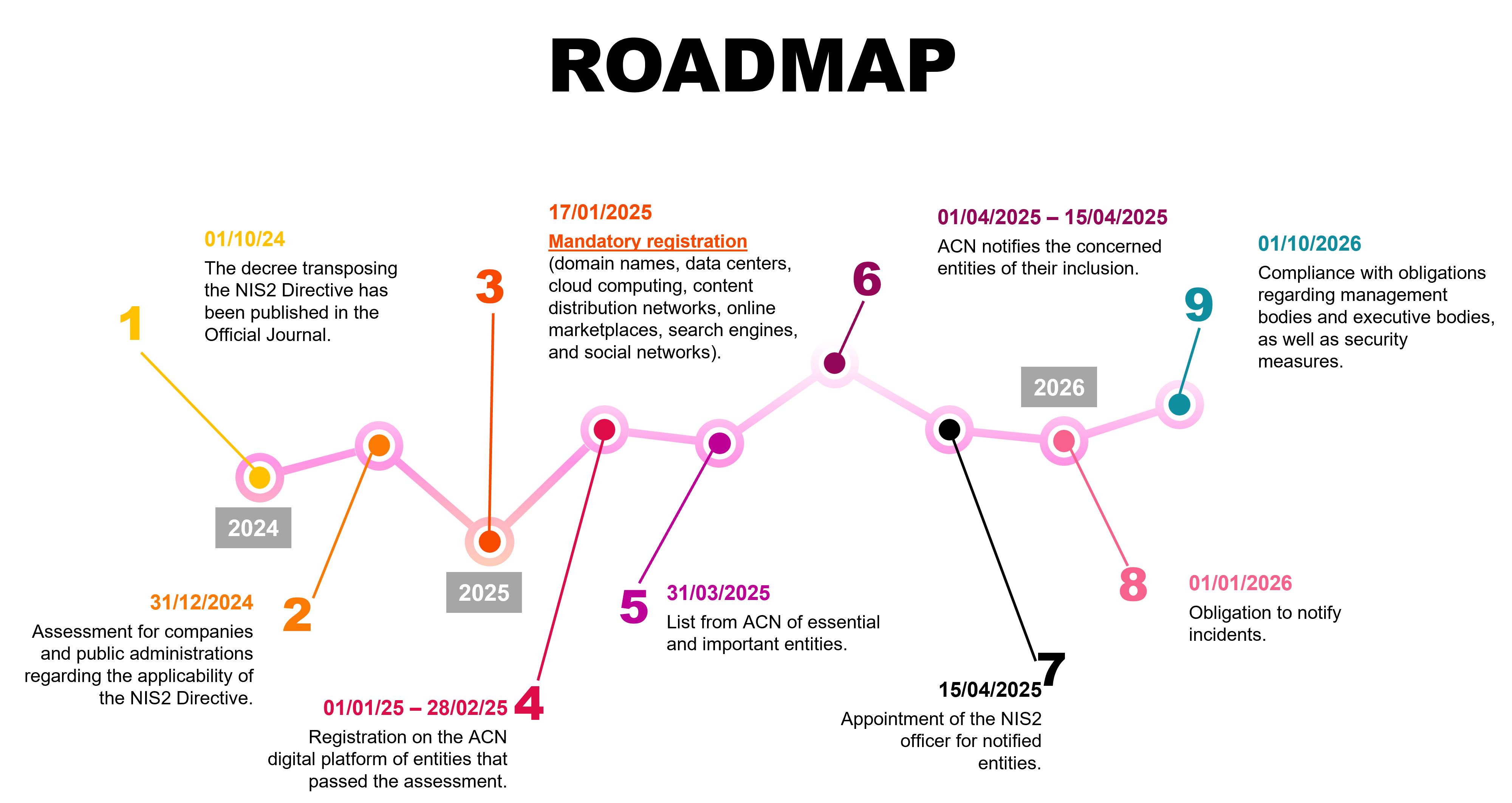
In response to the escalation of these threats, the European Union has adopted the NIS2 Directive, which enforces stricter security standards for critical networks and information systems.
The goal of this directive is to strengthen network defenses, improve data protection, and reduce risks associated with cyberattacks, ensuring greater security at both national and transnational levels.
SOLUTION
NIS2 Directive
The NIS2 Directive marks a milestone in Europe’s cybersecurity strategy, aiming to bolster the protection of networks and information systems on a continental scale. This regulation is designed to safeguard the digital infrastructure interconnecting businesses, institutions, and public administrations across Europe, ensuring the continuity and security of essential services for modern society. Compared to the earlier NIS Directive, which focused primarily on critical infrastructure in energy and transport sectors, NIS2 significantly broadens its scope, encompassing new crucial sectors such as digital services, healthcare, public administration, and industries producing essential goods.
Under the directive, organizations are categorized into two main groups: "essential" and "important." The former includes entities operating in sectors where information security is critical for societal functioning and national security. Among Net Reply's clients are numerous companies in the energy (ENERGY) and telecommunications (TELCO) sectors, which, due to their function, are subject to stricter security obligations. ENERGY companies involved in the production, transmission, and distribution of electricity are classified as "essential entities" because their activities are vital for maintaining the safety and stability of the country's key systems.
TELCO companies that operate critical infrastructure also fall into the category of essential players if they support emergency services, if their infrastructure is essential for the operation of vital national services, or if an interruption of their services would cause large-scale damage to society. Their role is therefore crucial not only for the economy, but also for crisis management and national security.
Prevention & Remediation
The NIS2 Directive mandates organizations to adopt a series of compulsory measures to improve Network Security, structured into two main areas: prevention and remediation. Prevention encompasses actions aimed at minimizing the risks of network attacks, while remediation focuses on strategies and measures to contain damage and quickly restore normal operations after an attack.
At a strategic level, every organization must develop policies and procedures to continuously assess the effectiveness of its security measures and its capacity to counter risks. A key component here is risk analysis: each organization must define clear security policies for network systems, implement regular evaluations of threats and vulnerabilities, and monitor the level of system protection continuously.
A top priority, especially for companies managing complex supply chains, is ensuring the security of the entire process, from supplier to end customer—commonly referred to as the supply chain. This must be protected at every stage, ensuring that all partners and suppliers adhere to required security standards.
Incident Management & Reporting
Employee training is another indispensable element. It is crucial for every staff member to be adequately trained on Network Security, acquiring skills to recognize and prevent threats while adhering to basic cyber hygiene practices. Companies must also implement access control policies and securely manage user identities, safeguarding access to sensitive data and critical resources.
At the operational level, securing systems involves protecting network assets at every stage of their lifecycle, from design to maintenance. Preventive measures include adopting encryption to protect sensitive data and implementing secure authentication to ensure that only authorized users can access systems.
When an attack occurs, the priority becomes ensuring business continuity, maintaining operations without significant disruptions. Measures such as backup management, crucial both as a preventive step and for post-attack recovery, play a vital role. Adopting disaster recovery plans is essential to ensure rapid data restoration and minimal operational interruption.
Network Incident Management
Another core aspect of the NIS2 Directive is managing Networking Incidents. Organizations must be prepared to respond swiftly to attacks, minimizing their impact on operations and data. This involves not only creating detailed incident management plans but also promptly reporting each breach and assessing its severity.
The NIS2 Directive outlines a precise protocol for incident reporting, divided into three key stages:
How Net Reply can support you
To ensure full compliance with regulations and robust protection against network security threats, Net Reply has developed a three-phase process aimed at enhancing the overall security of organizations:
The first phase involves an in-depth analysis of the organization's current Network Security measures. Existing processes and security strategies are evaluated to identify gaps relative to regulatory requirements and best practices. This step provides a clear overview of vulnerable areas requiring intervention.
After identifying vulnerabilities, the remediation phase addresses the identified issues. This includes technical interventions such as hardening systems to fix vulnerabilities and adopting new cybersecurity solutions. For instance, introducing advanced tools like multi-factor authentication (MFA), privileged access management (PAM), and intrusion detection systems (IDS). These actions may also involve changes to user procedures, aiming to enhance security in accessing corporate systems.
The final phase involves integrating corrective solutions into the client’s infrastructure. This step requires particular attention in complex architectural environments characterized by system heterogeneity and potential obsolescence. Careful planning is crucial to detail specific actions for each system and process, ensuring the seamless integration of remediations without compromising operational continuity.