)
Fraud detection is a crucial task in various industries such as finance, insurance, and e-commerce. A major problem, however, is the high rate of false positives in alerts. False positives occur when a legitimate transaction is flagged as fraudulent, causing inconvenience to the customer and wasting the resources of the organisation. False positives are caused by various factors such as inaccurate or incomplete data, outdated algorithms, manual intervention, and the lack of contextual information. In addition, fraudsters are getting more sophisticated in their techniques, making it harder for traditional rule-based systems to detect fraud accurately.
One way to reduce false positives is to implement machine learning algorithms that can learn from the data and improve over time. However, this also introduces new challenges such as the need for large amounts of high-quality data and the risk of model bias. Machine learning models have been implemented more generally in a retrospective context for fraud detection. This means that they are more geared towards reducing alerts associated with false positives rather than creating smarter alerts. Alternatively, another approach is to use network analysis techniques to detect fraud by identifying suspicious patterns of behaviour among connected entities such as customers, merchants, and devices. By analysing the relationships between entities, network analysis can uncover hidden fraud rings and other types of organised fraud.
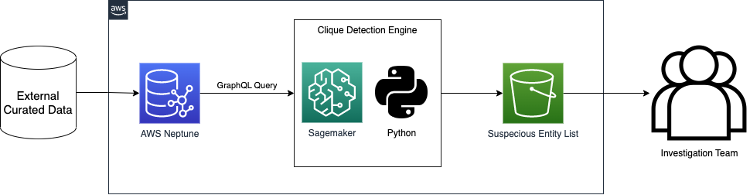
We first start with the original transaction network. The transaction network is imported into a cloud-based graph database, which is queried to retrieve a temporal slice of the original network.
We then perform a network reduction technique and remove potential middlemen and entities which we might not consider suspicious. We then focus our attention on the most densely connected sub-communities within the transaction network - these are the most likely to contain suspicious clique patterns. We are in search of patterns within a transaction network that is suspicious, we can call these patterns heavy cliques and are fully-connected sub-regions of a transaction network.
We run the recursive clique detection algorithm to find the suspicious entities. These patterns help identify suspicious entities in the wider transaction networks.
Output any suspicious entities into cloud-based storage for further analysis. We can run this process in a batch format every day, week, or month.
If you're interested in learning more about utilising network CLIQUE detection for advanced anti-money laundering, please get in touch.
Graph technology has been shown to perform better in fraud detection than traditional rule-based methods and has been made more available with the rise in computational power available, which allows users to have more precise and smarter alerts.
It can also integrate with existing systems, such as rule-based detection options, to provide a comprehensive view of financial transactions, allowing financial institutions to take faster and more informed decisions to prevent money laundering.
Rule-based systems can be further refined with clique detection running in parallel thereby reducing false positives and enhancing operational efficiency.
Fines amounting to millions of pounds could be mitigated by generating smarter alerts with a solution that costs a fraction of them, thereby reducing overhead.